Protect Accounts from Social Engineering
A social engineer can be anyone who can gain access to devices or a network by tricking people into providing the necessary information to cause damage. A social engineer may obtain the confidence of an employee to convince them to divulge username and password information or may pose as an employee in an attempt to gain entry to a facility. That is why it is important for companies to inform users about security policies such as never giving out your password, even if you get a call from your IT department. What about the user in the comfort of their home? I, unfortunately, live in a country with a worldwide reputation for scamming. The main one is known as the Lottery Scam. Many elderly victims in the United States, have been scammed into thinking they won the lottery; based on small snippets of information that might be available to the scammer; whether in a phone directory or left in a trash can outside your home or even online. Similar to the Nigerian Scams, many years ago, the bad guys can steal money without even meeting their victims. Scammers are notorious for looking up random names on the Internet; posing as agents informing a winner. The call usually requests the winner to send a certain amount of money to Jamaica, using money transfer services such as the Western Union; in order to collect their winnings. A scammer will not look or identify as a typical criminal. They tend to use well-spoken, young ladies, who serenade the victim into giving up their money.
A lot of our online engagement takes place in social networks, the most popular being Facebook. Today, Facebook is only one of the many available opportunities a social engineer can use to duplicate your identity. Instagram, WhatsApp, and other services can all be used as a means to infiltrate your network of friends and contacts. Open accounts, filled with pictures of you and your family are the perfect tools to create a profile that is as convincing as the real you. A social engineer could use your latest beach trip to contact a friend using the perfect story about being stuck on an island because you lost your credit card and had no cash to return home.
What can You Do to Prevent Becoming a Victim of Social Engineering?
Any social media account, where you share personal information such as family photos, vacation trips should be set to private; make it available only to people who you know and can verify. We discussed some of the ways you can lock down your Facebook account, the best option, of course, is to delete your account or never create one at all. However, that’s not realistic for a lot of people. Before uploading a photo to social media, check out our article on how to remove the info contained in the EXIF file it creates.
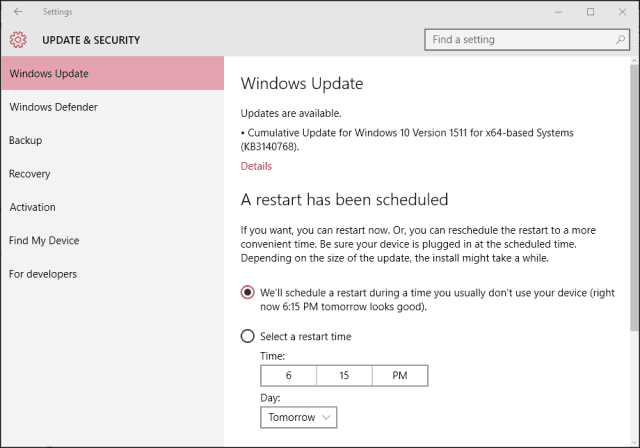
How to Remove Personal Data from Your Photos in Windows
Depending on where the risk exists, here are some measures you can use to protect yourself from social engineering. Never give out a password – not even to family members or co-workers. Always ask for the identification – If someone sends you an email, informing you that you just won the Powerball, use your common sense. Did you buy any lottery tickets or enter any raffles? Recently, I have been getting emails from Apple delivered to one of my alternate accounts; informing me my account was compromised and they need me to sign to resolve the issue. The message looks so real; you think it was actually from Apple, one simple look at the domain for the email address and I wondered when did Apple start using Hotmail as their official address.
Restrict access to unexpected visitors. If a stranger visits your home or place of work, you can limit access to just the gate, veranda, front porch or an open lounge area. Restrict the amount of information you give out and remain in control of the encounter. Ask for information such as identification; you can also take the information then call the company they are representing to seek further information about the individual or purpose of the visit. Escort all visitors. If a stranger visits your home or office, limit the amount of freedom they have to roam. If you work in an office environment or even at home, avoid common mistakes that can make it easy for someone to break into your account. Do not write a password on a note or stick it to your monitor or under your keyboard. I know it’s hard to memorize a good password, but the reality of losing sensitive data or having your account compromised is a significant loss in comparison.
Protecting Data
The objective of a social engineer is to harvest valuable data. Using a strong password can prevent unauthorized access to your information. Here are some tips you can use for implementing proper password policies: Use Two-factor authentication. This is especially handy in today’s world of travel and communication. Two-factor authentication creates multiple barriers to unauthorized access. For example, if you are signing into your email account from an unusual location, the email service can use the geographical location to determine your location-based GPS coordinates. The email service can request an additional point of verification such as a four-digit pin; sent to your cellular phone. Check out our comprehensive guide to using Two-factor Authentication.
Ensure your password expires after a particular time.Create a secure password containing a mixture of letters, numbers, and symbols.Lockout rules to limit the number of unsuccessful attempts.
Never leave your computer open at the office. Other users might be able to access it. A quick strike of the Windows + L command can lock your computer screen until you return. Data encryption. We previously looked at setting up and configuring encryption in Windows 10 both on the local drive and portable storage devices. Encryption helps to secure your data, making it unreadable to users; who do not have appropriate codes to access. This can be especially handy if a social engineer is successful; stealing your computer or thumb drive. Use a VPN. A Virtual Private Network is another technology we discussed in a recent article. A VPN connection allows a user to safely access resources on another computer remotely. Always Backup. Maintaining regular backups is a useful practice against data loss. Users should ensure frequent backups are performed. Securing your backups is also important; this can be done using the same encryption tools built into Windows 10.
Disposing of Sensitive Data
Dispose of sensitive information that can be utilized by social engineers to harvest personal data about you. Something as simple as the label containing your address on a product box placed in the trash outside your home.
Disposing of old computer devices is also important. An old hard disk or thumb drive must be properly destroyed. One way to do this is by using a hammer to shatter platters of the disk or thumb drive. I know it’s a bit primitive, but it’s the next best thing you can do. Old credit cards are another vector that can be used to harvest information about you. Investing in a cross shredder can help to destroy both credit cards, optical discs, and sensitive documents.
Online Identities
Creating an alternate online identity can be an important key to protecting your personal information and privacy. You can have multiple email accounts and aliases; that are used for different purposes. For instance, you can have a throwaway email just for newsletters and websites you sign into; without the need to disclose any personal information. Popular webmail services such as Outlook.com, Google’s Gmail, and Apple’s iCloud all support creating alias accounts. An extra layer of security you can integrate when setting up a new account is to provide fake answers to security questions like what’s your favorite sports team or first girlfriend. This will certainly minimize the chances of the account becoming compromised if a social engineer knows a bit about you.
Keep your Operating System and Applications Updated
Regular security updates are a critical part of protecting your information; from attackers searching for new ways of breaching it. The Internet has changed the game of how we approach security. We recently discussed some of the changes to the maintenance experience in Windows 10. When using devices such as tablets, smartphones, or desktop computers; installing the latest updates is an important part of staying ahead. Develop a habit of recognizing new updates and patches, then install them immediately when they are released.
Mobile Devices
We store some of our most sensitive information on mobile devices; such as smartphones and Tablets. Keeping these devices safe has become a top priority of mobile operating system developers and hardware vendors. Apple three years ago introduced Touch ID on the iPhone 5s; while Samsung and many other brands have introduced their biometric technologies. Make sure you take advantage of these built-in security mechanisms. Anyone who gets access to your phone can quickly view your emails, contacts, and any other sensitive information you might store on it.
Online Behavior and Activity
Your activities online have a significant impact on your safety. Downloading content from individual websites or even using torrent clients can open your computer to malicious code. Some torrent software makes it easy for rogue software to piggyback on your device. Legitimate software such as JAVA or WinZip will install add-ons that are difficult to remove. Read the on-screen instructions carefully when installing these applications. Keep track of your bank statements regularly and look for any signs of usual activities such as expenses you are not aware of making. Contact your bank immediately in the event of such incidents. Cultivating a behavior of skepticism and being circumspect with what you share and applying certain strategies will make you less of a target for social engineers. Privacy is a critical part of our computing activities that can be lost by voluntary disclosure. This is a lot of information to take in, so here is a summary of what we discussed.
Security threats can come from inside or outside of an organization.Developing and maintaining a security plan to protect both data and equipment from loss is important.Keeping your operating system and applications updated keeps you ahead of the game. Social engineers and hackers are constantly checking for cracks, always keep that in mind.
Do you have other suggestions? Leave a comment in the section below and share it with us. Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.
![]()